How to check the phone for wiretapping
 Over time, the question of how to check the phone for wiretapping arises among users more and more often, because technology is constantly progressing, which leads to the inevitable emergence of new spy utilities. At the moment, absolutely every smartphone owner can determine the fact of the presence of wiretapping on the phone - we will talk about how to do this in the article.
Over time, the question of how to check the phone for wiretapping arises among users more and more often, because technology is constantly progressing, which leads to the inevitable emergence of new spy utilities. At the moment, absolutely every smartphone owner can determine the fact of the presence of wiretapping on the phone - we will talk about how to do this in the article.
Phone tapping signs
Before proceeding with the use of methods for detecting wiretapping, it is worth paying attention to several key signs of listening to a smartphone.

If most of the factors below are true, then the likelihood of spyware is quite high:
- Strong heating of the smartphone and fast battery discharge. If your device gets warm after you haven't used it for an hour (it's been locked, not charging, and not doing complex calculations), it might be due to a spy app running in the background.
- Failures and errors in work. Usually, the installed wiretap causes regular system errors, crashes, failures and automatic reboots, accompanied by appropriate notifications.
- Independent launch of applications. If sometimes the smartphone spontaneously launches "Messages" or any other applications related to personal data, you need to check for wiretapping.
- Interference in conversation. The appearance of extraneous noise and constant interruptions in communication may indicate the appearance of spyware on the smartphone.
Expert opinion
Daria Stupnikova
Specialist in WEB-programming and computer systems. PHP/HTML/CSS editor for os-helper.ru site .
Ask Daria It is not necessary to draw unambiguous conclusions on the grounds presented above - their presence only indirectly indicates the possibility of wiretapping.
Verification methods
If all the facts indicate that the phone can indeed be tapped, you need to start checking.
See also: How to find the phone if it is turned off
USSD commands
With the help of certain commands entered in the dialing field, you can find out how secure the connection to the network is:
- *#43# - shows if the phone is connected to another device to which information will be transmitted.
- *#21# - gives information about whether call forwarding is configured (usually wiretapping is carried out by forwarding a call to a spy number).
- *#62# - almost the same as the previous command, indicates the redirection activity in the absence of access.
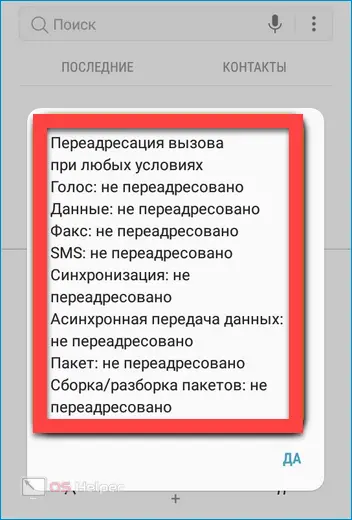
Using the ##002# command, you can immediately disable all types of call forwarding - this will increase your privacy and prevent the call from being transferred to third parties.
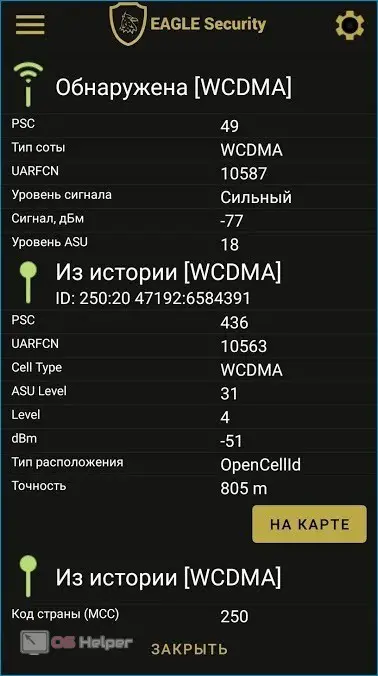
Eagle Security
Eagle Security is a simple application that allows you to detect wiretapping on your phone.
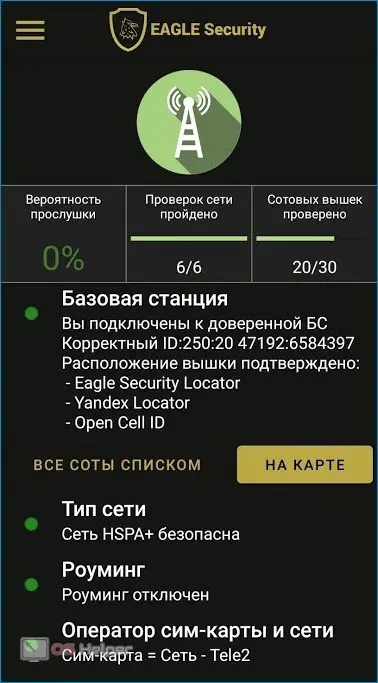
Download and install the program, open the side menu, go to the "Spyware" item and get acquainted with the list of detected spyware. If the program finds suspicious applications, you can stop them.
Incognito
Incognito is a utility similar to the previous one, capable of automatically searching for various types of spyware modules.

After installation, you just need to click on the "Start Scan" button and wait for the results of the analysis. If the utility finds suspicious software, it will provide detailed instructions on how to remove it.

Dr. Web
You can check your smartphone with any antivirus convenient for you, however, we will detect wiretapping using the free Dr. Web. Install the application, click on "Scanner" and run a full scan.
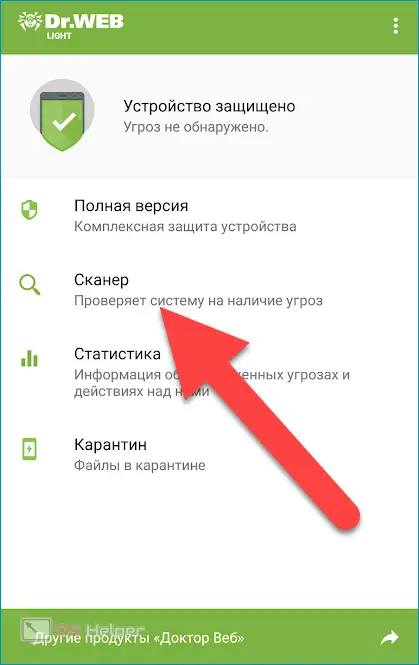
At the end of the scan, the antivirus will compile a list of threats. To go to manage them, you need to click on the symbol in the form of a lightning bolt. It is advisable to immediately remove all found spy utilities.
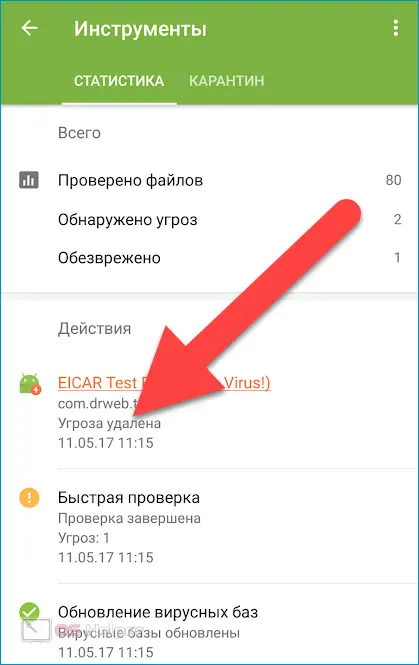
You can ignore the request of the antivirus only if you installed the application to be removed yourself (perhaps an error occurred during the check).
Video instruction
Below is a video that details the signs of listening to a smartphone.
Also Read: How To Quickly Discharge Your Phone
Conclusion
If the methods presented in the article did not reveal wiretapping, but at the same time you still have suspicions, you should provide the device to a specialist in the field of digital security - only a professional can give an accurate and reliable conclusion.